Implement EIP-7730 today
The recent $1.5 billion Bybit hack has exposed a critical vulnerability in the Web3 ecosystem that the community has largely overlooked for years. While Bybit’s compromised supply chain and failure to verify signatures on a separate device were the immediate causes, this incident highlights broader security challenges affecting all wallet users, not just major exchanges.
As industry professionals, we must ask, do typical users have enough information to safely validate their transactions? The uncomfortable truth is no. The current expectation that users should cross-check signatures across multiple devices is unrealistic for mainstream adoption. Few, if any, users routinely verify calldata using multiple verification methods before signing transactions. We previously explored these wallet UX limitations in our custodial stablecoin rekt test, where we highlighted how unrealistic current verification expectations are for typical users.
In this post, we’ll demonstrate how dapp developers can help protect their users from blind signing issues using EIP-7730, which enables hardware wallets to decode transactions and allows users to understand what they are really signing.
We believe that dapps that support EIP-7730 will have a huge edge over their competitors. As the number of high-profile hacks involving blind signing increases, users will demand improved security assurances from the dapps they choose to interact with.
Why blind signing creates an impossible security burden
Consider the security steps users need to follow for each transaction:
- Verify the transaction’s calldata matches the intended action on their primary workstation
- Confirm that the transaction hash on their workstation matches the one on their hardware wallet
- Cross-check on a separate workstation that the transaction hash and its decoded calldata correspond to their intended action
While theoretically secure, this multi-device verification process creates insurmountable friction for average users, requiring several minutes to rigorously cross-check each transaction across multiple devices. Security cannot come at the expense of usability if we expect dapps to achieve mainstream adoption.
The problem of blind signatures
The core issue lies in blind signatures: asking users to sign data they cannot meaningfully interpret. This happens because wallets lack the protocol-specific knowledge needed to decode transaction data into human-readable formats. Each DeFi protocol has its own unique smart contract interfaces and parameter structures, but wallets cannot understand what these technical parameters actually mean without explicit instructions for interpretation. Would you sign a legal contract without reading its contents? Yet in Web3, users regularly sign cryptographic hashes that appear as unintelligible strings:
0x3b812a5cf28be8e4787e1d1d4d513744966d8684da2f9a61187a79607c1b9fcaUsers resort to this because they often have no alternative when interacting with certain protocols. Most wallet implementations offer raw signing as a supposedly better option, where you sign non-decoded format information. For example:
0x0000000000000000000000008c1ed7e19abaa9f23c476da86dc1577f1ef401f50000000000000000000000007a250d5630b4cf539739df2c5dacb4c659f2488dffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000063ae3c1fHowever, to make informed signing decisions, users need to understand critical transaction details: the exact amount of funds being transferred, swapped, or deposited, the destination addresses, the type of operation being performed, any associated risks like slippage tolerance or delegation permissions, etc. Without these details, the user is essentially trusting their workstation to send a non-malicious transaction to their hardware wallet, creating a dangerous dependency on potentially compromised systems.
This brings us back to our original blind signature problem: users signing data representations they cannot verify or understand.
A step forward with EIP-712, but not enough
EIP-712 was originally introduced specifically to address the blind signing problem by providing a standardized way for applications to present structured, human-readable data to users before signing. This standard works by defining a structured data format that wallets can interpret and display, allowing users to see organized fields like token amounts, recipient addresses, and operation types instead of raw cryptographic data. The protocol achieves this by requiring applications to provide both the raw transaction data and a structured schema that describes what each piece of data represents, enabling wallets to render meaningful information to users.
This standard allows users to verify individual fields they’re signing, theoretically enabling “clear signing” instead of blind signing.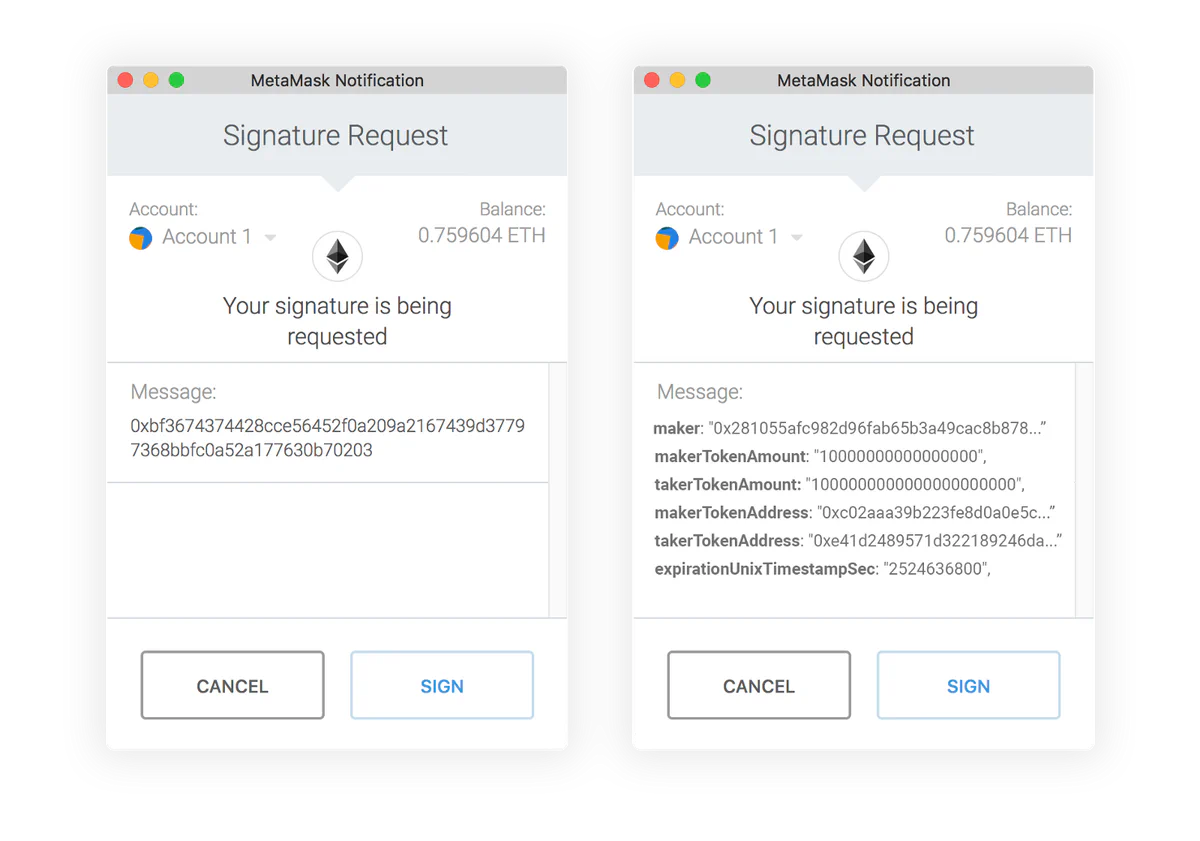
While EIP-712 represents significant progress by standardizing structured data signatures across many protocols, it still falls short in critical ways. The Bybit hack clearly demonstrates these limitations. Despite supporting EIP-712, the transaction data remained too complex for human verification. In the compromised transactions, some parameters of the signature input were changed, most crucially the operation type from 0 (normal call) to 1 (delegate call), along with the destination address.
Here is the compromised information they signed: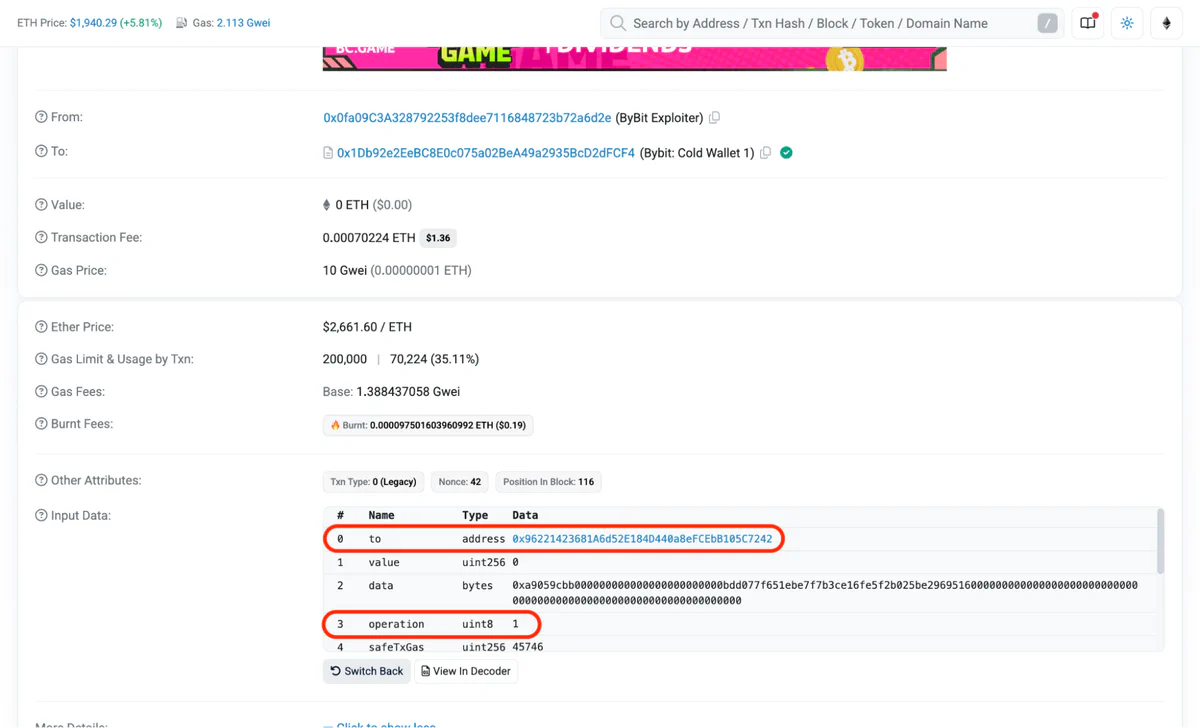
This subtle difference in operation type completely changed the transaction’s behavior, allowing the attacker to execute malicious code in the context of the Safe contract. These technical details would be nearly impossible for most users to detect when confronted with hex-encoded values that provide no human-readable context.
What signers likely saw in their wallets was slightly different representations of the EIP-712 data structure. While some hardware wallets like Trezor Model T do support EIP-712 and can display the structured message, the standard doesn’t address the challenge of rendering nested operations in a human-readable format. The wallet would need specialized knowledge that the “data” parameter represents a calldata operation requiring further decoding.
Even when compared side-by-side in interfaces like MetaMask, the original and tampered transactions would appear similar enough that users could easily mistake one for the other without a deep technical understanding of the underlying parameters. The most crucial change, the operation type switch to delegatecall, was particularly difficult to identify without specialized knowledge.
This highlights that while EIP-712 provides structure, these complex transactions must be further decoded into truly human-readable formats. Without this additional layer of interpretation, users are still effectively blind signing data they cannot meaningfully validate.
Hardware wallets provide an incomplete solution
Laptops, phones, and computers can all be compromised. Hardware wallets are more secure since they are designed only to sign transactions and keep secret keys secure. They have the least chance of being compromised. However, while computers can display rich user interfaces, hardware wallets have very simple and minimalist UX that cannot be modified by websites requesting signatures. However, hardware wallets don’t have the ability to decode anything other than the simplest transactions. This is because they lack the semantic information required to decode what will happen when a specific contract function is called. For example, calling the transferFrom function on a normal ERC-20 may have a different result than calling transferFrom on a contract that implements fee-on-transfer.
Some hardware wallet manufacturers like Ledger have attempted to address this through dedicated plugins. When interacting with supported protocols like Paraswap, users can download specific apps to their hardware wallets, enabling them to view transaction details directly on their secure device, bypassing any compromised information on their computer.
Yet this approach faces a critical adoption gap. Of the hundreds of DeFi applications, fewer than 200 have dedicated Ledger apps1, with many being simple wallets rather than dapps. Major DeFi protocols are conspicuously absent.
A significant factor in this limited adoption is the substantial investment required to develop these plugins. Protocol teams often avoid creating hardware wallet integrations due to the considerable time and financial resources needed. Developing, testing, and maintaining these specialized applications requires dedicated engineering talent and ongoing support for each of the hardware wallets on the market, resources that many protocols prefer to allocate toward feature development, liquidity incentives, or other growth initiatives. However, this cost-benefit calculation fails to properly weigh the critical security implications of blind signatures.
The path forward with EIP-7730 and beyond
Fortunately, a promising solution is on the horizon. EIP-7730 represents a critical initiative to eliminate blind signing by enabling true “clear signing” with minimal protocol implementation burden.
This approach drastically increases the efficacy of transaction verification. Since the hardware device can directly parse the content of each message with explicit instructions on what to display and how, users can see human-readable information instead of cryptographic gibberish. Imagine seeing this technical data:
uint256 amountIn: 500000000000000000
uint256 amountOutMin: 800000000
uint256 slippageBps: 100
uint256 deadline: 1715157000Transformed on your hardware wallet screen into: Swap 0.5 ETH for minimum 800 USDC (1% slippage protection) - Valid until May 8, 2024 at 8:30 AM.
This improvement in clarity enables truly informed consent by translating technical parameters into concepts users actually understand.
The critical security advantage is that this information appears on a fully isolated hardware device that cannot be compromised by malware without exploiting a vulnerability on the hardware wallet itself.
Users can be more confident that what they see on their hardware wallet is precisely what they’re signing. No compromised supply chain or workstation can tamper with the transaction without altering its semantic description. If the description doesn’t match their expectations, they can simply reject the transaction.
What makes EIP-7730 game-changing is how simple it is for developers to implement. Rather than developing complex hardware wallet integrations, protocols need only provide a JSON file to whitelist their contract on device registries. This standardized approach dramatically reduces the technical barriers that have prevented widespread adoption of secure signing practices. From the protocol point of view, the entire implementation process could be as simple as submitting a pull request with the appropriate JSON file.
EIP-7730 in practice
To demonstrate how straightforward EIP-7730 implementation can be, let’s walk through creating a JSON manifest for a basic token swap function. Consider this Solidity function from Uniswap V3:
function swapTokensForExactTokens(
uint amountOut,
uint amountInMax,
address[] calldata path,
address to,
uint deadline
) external returns (uint[] memory amounts);With EIP-712, users would see structured but still technical data on their wallet:
Domain: Uniswap V3 Router 2
amountOut: 800000000
amountInMax: 800000000000000000000
path: [0xa0b86991c6218b36c1d19d4a2e9eb0ce3606eb48,
0x6b175474e89094c44da98b954eedeac495271d0f]
to: 0x742d35Cc6634C0532925a3b8D5c5E3e7e7e7e7e7
deadline: 1715157000While this is better than raw hex data, users still need to:
- Manually convert
800000000to USDC amount - Convert
800000000000000000to DAI amount - Look up token addresses to understand what tokens are being swapped
- Convert the timestamp to a readable date
- Verify the recipient address matches their wallet
With EIP-7730, developers can create a simple JSON manifest that transforms this technical data into a truly human-readable format. Here are the steps:
- Clone the
clear-signing-erc7730-developer-toolsrepo - Go to the
/developer-previewdirectory - Install dependencies with
npm i - Create and add the JSON file to the registry folder
{
"context": {
"$id": "Uniswap v3 Router 2",
"contract": {
"deployments": [
{
"chainId": 1,
"address": "0x68b3465833fb72A70ecDF485E0e4C7bD8665Fc45"
}
],
"abi": "https://github.com/LedgerHQ/ledger-asset-dapps/blob/211e75ed27de3894f592ca73710fa0b72c3ceeae/ethereum/uniswap/abis/0x68b3465833fb72a70ecdf485e0e4c7bd8665fc45.abi.json"
}
},
"metadata": {
"owner": "Uniswap",
"info": {
"legalName": "Uniswap Labs",
"url": "https://uniswap.org/"
}
},
"display": {
"formats": {
"0x42712a67": {
"$id": "swapTokensForExactTokens",
"intent": "Swap tokens",
"fields": [
{
"path": "amountOut",
"label": "Amount to Receive",
"format": "tokenAmount",
"params": {
"tokenPath": "path.[-1]"
}
},
{
"path": "amountInMax",
"label": "Maximum Amount to Send",
"format": "tokenAmount",
"params": {
"tokenPath": "path.[0]"
}
},
{
"path": "to",
"label": "Recipient of the output tokens",
"format": "addressName",
"params": {
"sources": ["local"]
}
},
{
"path": "deadline",
"label": "Valid until",
"format": "date"
}
]
}
}
}
}- Run locally with
npm run dev
The user now sees:
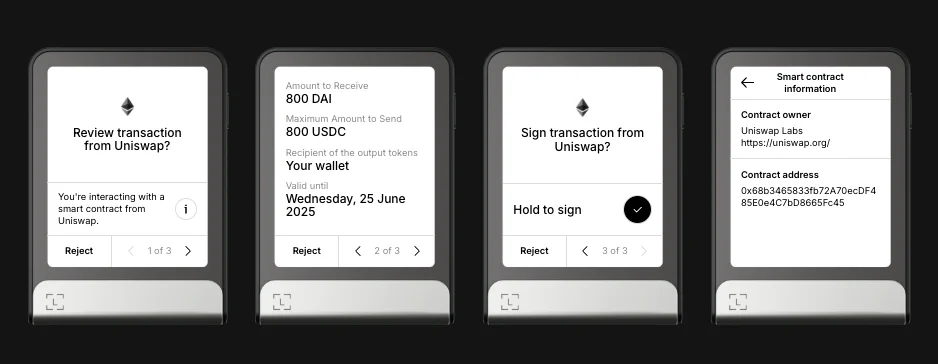
6. Add the JSON to the official repository
The entire implementation process involves creating this JSON file and submitting it to the registry. No complex integrations, no custom hardware wallet development, just a straightforward manifest that makes your protocol’s transactions human-readable.
This approach scales to any protocol complexity while maintaining the same simple implementation pattern, making secure signing accessible to every dapp in the ecosystem.
Implement EIP-7730 today
The path to eliminating blind signatures in your protocol is now straightforward and accessible. As a dapp developer, you can dramatically improve your users’ security and experience in just a few hours of implementation work.
Getting started is simple:
- Use Ledger’s development tool: Ledger has developed a comprehensive tool that streamlines JSON manifest creation at https://get-clear-signed.ledger.com/. This tool guides you through the entire process, making EIP-7730 implementation accessible even for teams without extensive cryptographic expertise.
- Submit your integration: Once your JSON manifest is ready, create a pull request to add it to the Ledger registry repository at https://github.com/LedgerHQ/clear-signing-erc7730-registry. This centralized registry ensures discoverability while maintaining security standards. Note that registry ownership will transition to a foundation-operated model in the future, similar to the Ethereum Chain ID list, striking the optimal balance between decentralization and discoverability.
- Professional review process: After submission, Ledger’s security team will review your manifest within a few days. This review ensures that your implementation accurately represents transaction data without hiding critical information or using misleading terminology. Only non-malicious, properly functioning manifests are approved.
- Launch clear signing: Once your manifest is approved, clear signing functionality becomes available for your protocol immediately. Your users will see human-readable transaction details on their hardware wallets.
That’s all! You’ve changed your users’ experience by eliminating the anxiety and fear that comes with blind signing, transforming their Web3 experience from one of uncertainty to genuine confidence.
While EIP-7730 significantly improves transaction security by eliminating blind signing, the most direct attack vector for hackers remains exploiting vulnerabilities in smart contracts themselves. Even with perfect transaction transparency, users can still lose funds if the underlying protocol contains security flaws.
If you’re unsure about your smart contract security posture, Trail of Bits can help. Our team has audited hundreds of DeFi protocols and can identify vulnerabilities before they’re exploited in production. Contact us to learn how we can help build security into your protocol, alongside implementing EIP-7730 for comprehensive user protection.
1 Source: Ledger Live App (June 6, 2025)
