Exploiting zero days in abandoned hardware
We successfully exploited two discontinued network devices at DistrictCon’s inaugural Junkyard competition in February, winning runner-up for Most Innovative Exploitation Technique. Our exploit chains demonstrate why end-of-life (EOL) hardware poses persistent security risks: when manufacturers stop releasing updates, unpatched vulnerabilities remain frozen in time like fossils, creating perfect targets for attackers.
Both of the devices we exploited, a Netgear WGR614v9 router and a BitDefender Box V1, were fairly popular devices designed to protect your home network. But since both have gone years without updates, we were able to fully exploit them remotely from the local network.

With the second DistrictCon Junkyard competition being announced for early 2026, we would like to share our experience and research from the first one. Our full analysis is available on the Trail of Bits exploits repo for readers interested in the complete technical details.
First, we developed three ways (videos 1, 2, and 3) to hack the Netgear router by chaining multiple LAN-side vulnerabilities in the UPnP daemon, including authentication bypass, buffer overflows, and command injection, which gave us a remote root shell. We then exploited the Bitdefender Box (video) by leveraging a LAN-side unauthenticated firmware downgrade vulnerability combined with command injection in the firmware validation process, which also gave us a remote root shell.
Device analysis and firmware extraction
For the Netgear device, we disassembled it and identified debugging interfaces, data storage chips, and the SOC. Since Netgear provides firmware online, we downloaded it rather than extracting it ourselves. We used binwalk and unblob to recursively unpack the firmware, ran a port scan to identify interesting network services, and logged in to the serial console to check running processes, LAN-facing services, CPU specs, kernel version, and enabled mitigations. We initially looked at httpd but then pivoted to upnpd.
For the Bitdefender Box V1, we found a serial port, but the shell was locked down. We managed to extract firmware through the SPI flash chip and tried to get the latest version by reverse engineering the update mechanism, but the update servers were offline. We found what we think is the latest version by scraping APK mirroring websites since the firmware was included in the APKs. Without a shell on the device, we emulated the httpd binary locally using QEMU user mode for dynamic testing.
Exploiting the Netgear router’s UPnP
The Netgear WGR614v9 router runs a MIPS32-based system with multiple network services. After connecting to its UART interface (the serial debug port exposed on the board as “JP1”), we gained low-level system access during the boot process.
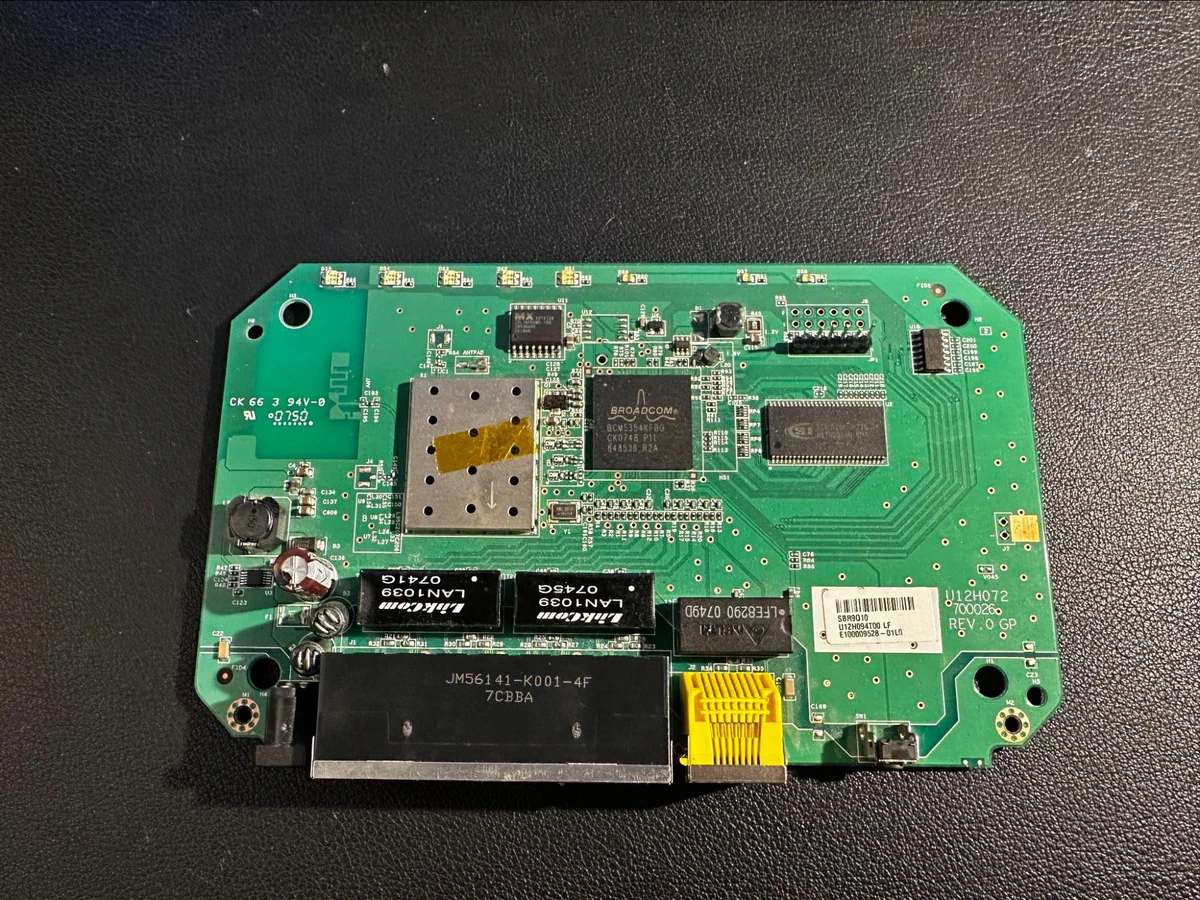
We focused on the Universal Plug-and-Play (UPnP) daemon: a service designed to simplify device discovery and configuration on networks. UPnP accepts SOAP messages (XML-formatted commands) to control router functions, making it a prime target due to its complex parsing requirements and privileged system access.
After completing our analysis, our exploitation chain leveraged four vulnerabilities:
- An authentication bypass in the SOAP message handler that allowed password resets
- Three buffer overflow vulnerabilities in both the BSS and stack memory regions
In our first exploit, bashsledding, we showcase an interesting variation of the classic nopsled technique. After discovering two ROP gadgets that can invoke “system,” we sprayed our shell command payload into NVRAM, which is memory-mapped into all processes, through the router’s domain-blocking feature. By prepending sequences of spaces (our “nops”) before the command and regardless of the exact landing position, the bash interpreter would harmlessly process spaces until reaching our command, creating a “sled” of valid shell syntax rather than CPU instructions. This technique provided reliable code execution.
The last exploit we demonstrated, bigfish_littlepond, cleverly pivots a limited memory corruption bug into a stronger command injection. The BSS overflow is used to modify an adjacent string pointer representing shell commands. Given the presence of the “bpa_monitor” string in upnpd and an exploitable command injection in that binary, we changed it to launch the bpa_monitor binary. An additional request containing our injection payload allows for full code execution.
You can find the full exploit code and writeup on GitHub, as well as videos for bashsledding, break_block_bof (our second exploit, not mentioned here), and bigfish_littlepond.
Breaking the Bitdefender Box with outdated firmware
The Bitdefender Box v1 represents an ironic target: a security appliance designed to protect home networks from threats, discontinued in July 2021. Created around 2017, it was part of a trend of AV vendors expanding into hardware security devices with subscription models.
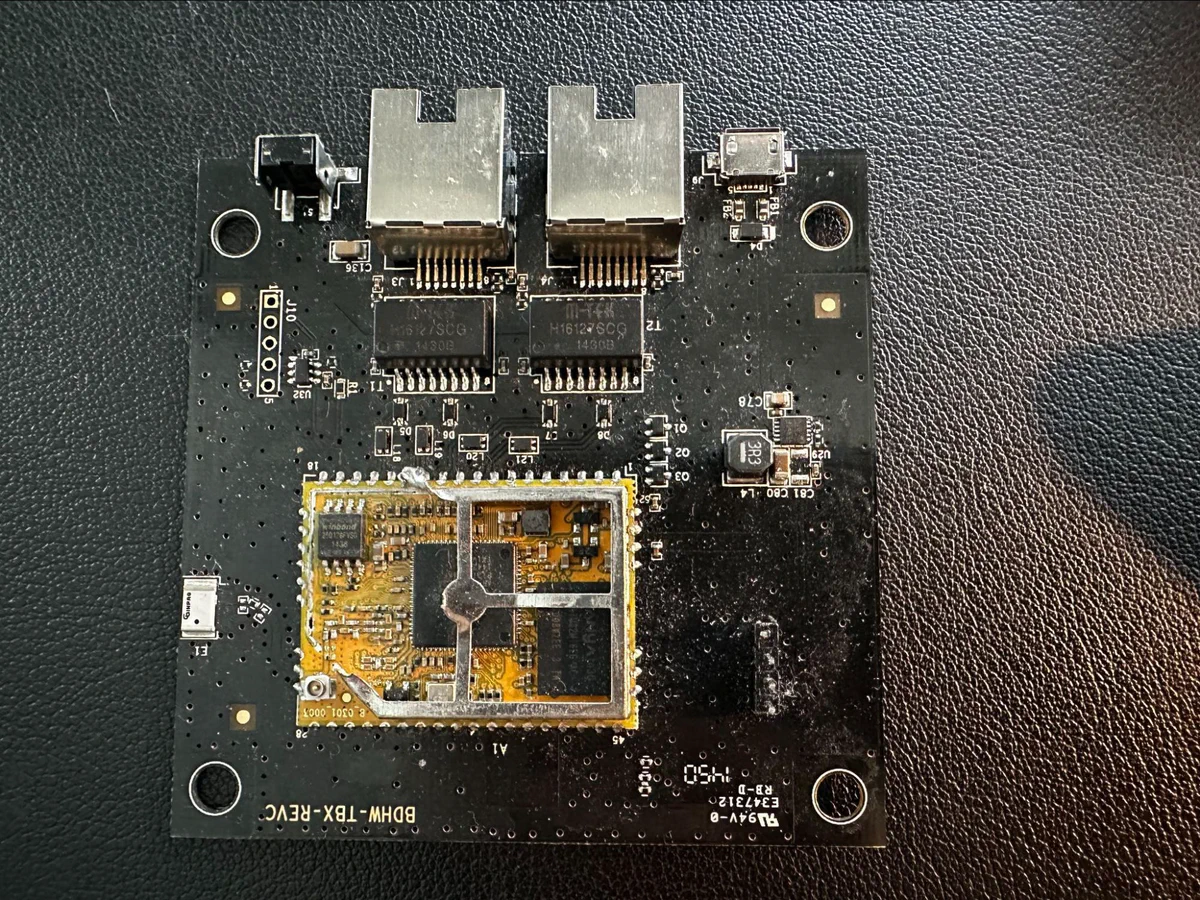
The device functions by inserting itself into the network path, overriding DHCP settings and redirecting traffic through its proxy to scan for threats. Despite its security focus, we found a completely unauthenticated firmware update mechanism.
Our hardware analysis revealed a Winbond W25Q128FV SPI NOR flash chip, which we accessed using an SOP8 clip with an XGecu T48 programmer to extract the firmware. The firmware analysis revealed a Lua-based web server with multiple HTTP endpoints used by the companion mobile app.
The exploit chain we developed used the following endpoints:
- The
/update_auth_tokenendpoint, which had a side effect of clearing configuration files that would prevent firmware updates - The
/upload_backup_firmwareendpoint to upload a Base64-encoded firmware image - The
/decode_imageendpoint to decode and verify the firmware’s basic structure - The
/check_image_and_trigger_recoveryendpoint with a vulnerablemd5parameter
While the device implemented signature verification for firmware updates using an RSA public key, we discovered that Bitdefender distributed old firmware images within their mobile app APKs. By locating an ancient APK (version 1.3.12.869) on VirusTotal, we recovered firmware version 1.3.11.490 with its valid signature.
Diffing this old firmware against newer versions revealed a basic command injection vulnerability in the md5 parameter: a classic case of string interpolation without proper filtering. The newer firmware implemented a validation function that filtered characters like semicolons, quotes, pipes, and parentheses, but this protection was absent in the older version.
By downgrading to the vulnerable firmware and exploiting the command injection, we added our SSH public key to the device’s authorized_keys file, gaining persistent access to the entire system.
Just checksumming and signing firmware updates isn’t enough. Without robust version verification and authenticated update processes, validating cryptographic signatures alone can’t prevent downgrade attacks.
You can find the full exploit code and writeup on GitHub, and a video on YouTube.
Security implications beyond the competition
We’re already looking forward to next year’s Junkyard competition! In the meantime, consider this a reminder to check if your smart devices are EOL, and exercise caution if they are; research manufacturers’ support timelines before purchasing new devices; and seek open-sourced alternatives.
The vulnerabilities we discovered represent broader patterns in IoT security. UPnP implementation flaws aren’t unique to the Netgear router and can plague other manufacturers and devices. Firmware downgrade vulnerabilities like those in the Bitdefender Box highlight how supposedly secure update mechanisms often lack critical protections, such as downgrade prevention.
If you have an EOL device, it may not be necessary to throw it away, but you should consider the risks of continuing to use it. For consumers, this necessitates careful consideration not just of a device’s features but its entire security lifecycle, including manufacturer support commitments and community firmware options.
For researchers and security practitioners, EOL devices represent both valuable learning opportunities and potential security blind spots in networks. The Junkyard Competition is great for bringing these kinds of devices into the spotlight, where there is much to learn about how manufacturers deprecate their technologies. It’s more approachable than high-stakes competitions like Pwn2Own, which makes it a great venue for researchers to participate and improve their skills.
Choosing a target
Picking the right end-of-life devices helps when you’re doing research for competitions like Junkyard. The requirements are straightforward: the device must no longer be supported by the manufacturer, and the devices should be cheap enough to buy several of them. It’s always helpful to have spares, especially when targeting hardware: devices may come with different firmware versions or varying conditions when purchased secondhand, or you may need a backup because you destructively took it apart or because you accidentally bricked the device (at least one of these things happened to us).
We targeted devices that seemed likely to have interesting vulnerabilities without needing months of reverse engineering. Debug interfaces aren’t required, but they make analysis much easier. What matters more is having some way of getting the firmware: some manufacturers publicize firmware downloads on their websites, while others require extracting it from the device. SPI chips are much easier to work with, but extracting firmware from eMMC requires specialized tools.
Before purchasing devices, it’s important to do some research online. Check the manufacturer’s website for firmware downloads, look for existing security research, and look up FCC filings to get a peek at what’s inside the device.
