The $1.5B Bybit Hack: The Era of Operational Security Failures Has Arrived
Two weeks ago at the DeFi Security Summit, Trail of Bits’ Josselin Feist (@Montyly) was asked if we’d see a billion-dollar exploit in 2025. His response: “If it happens, it won’t be a smart contract, it’ll be an operational security issue.”
Today, that prediction was validated.
The Attack
On February 21, 2025, cryptocurrency exchange Bybit suffered the largest cryptocurrency theft in history when attackers stole approximately $1.5B from their multisig cold storage wallet. At this time, it appears the attackers compromised multiple signers’ devices, manipulated what signers saw in their wallet interface, and collected the required signatures while the signers believed they were conducting routine transactions.
This hack is one of many that represent a dramatic shift in how centralized exchanges are compromised. For years, the industry has focused on hardening code and improving their technical security practices, but as the ecosystem’s secure development life cycle has matured, attackers have shifted to targeting the human and operational elements of cryptocurrency exchanges and other organizations.
These attacks reveal an escalating pattern, with each compromise building on the last:
- WazirX Exchange ($230M, July 2024)
- Radiant Capital ($50M, October 2024)
- Bybit Exchange ($1.5B, February 2025)
In each case, the attackers didn’t exploit smart contract or application-level vulnerabilities. Instead, they compromised the computers used to manage those systems using sophisticated malware to manipulate what users saw versus what they actually signed.
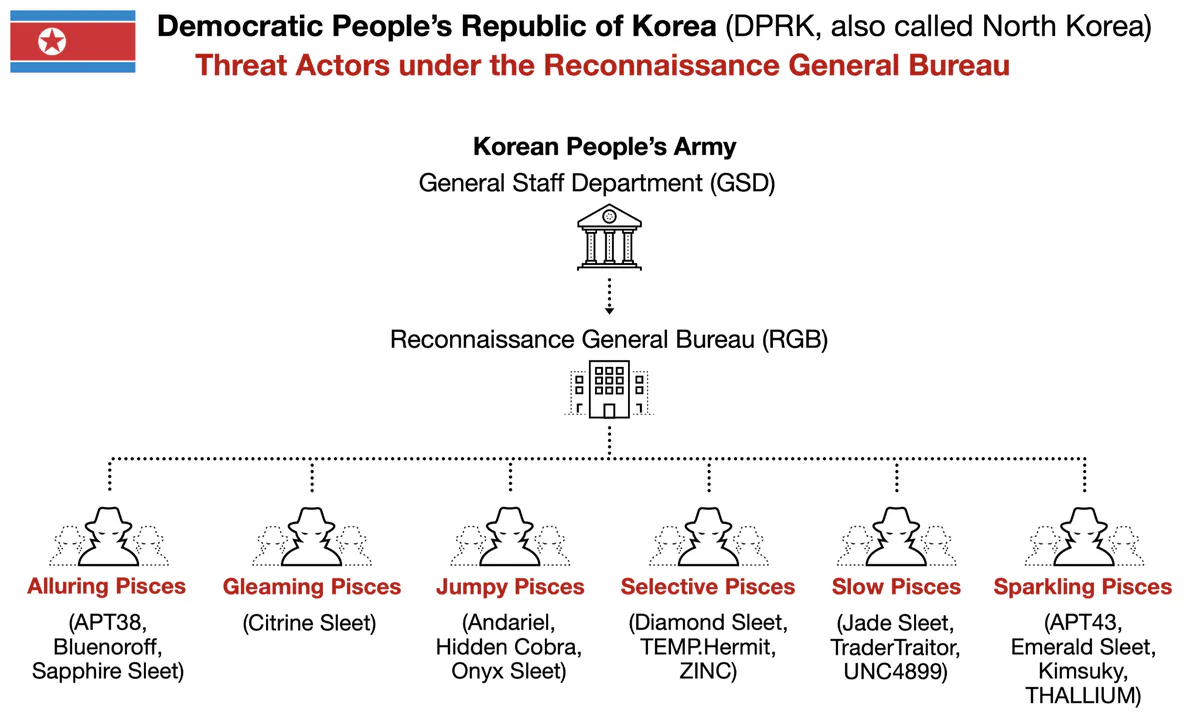
The DPRK’s Cryptocurrency Theft Infrastructure
These hacks are not isolated incidents. According to Arkham Intelligence, famed researcher ZachXBT has provided definitive proof linking this attack to North Korea, including detailed analysis of test transactions and connected wallets used ahead of the exploit. These incidents represent the maturation of sophisticated attack capabilities developed by North Korean state-sponsored threat actors, specifically groups tracked as TraderTraitor, Jade Sleet, UNC4899, and Slow Pisces under the DPRK’s Reconnaissance General Bureau (RGB).
The attack chain typically begins with aggressive social engineering campaigns targeting multiple employees simultaneously within an organization. The RGB identifies key personnel in system administration, software development, and treasury roles, then creates detailed pretexts - often elaborate job recruitment schemes - customized to each target’s background and interests. These aren’t mass phishing campaigns; they’re meticulously crafted approaches designed to compromise specific individuals with access to critical systems.
What makes these attacks particularly concerning is their repeatability. The RGB has built a sophisticated cross-platform toolkit that can:
- Operate seamlessly across Windows, MacOS, and various wallet interfaces
- Show minimal signs of compromise while maintaining persistence
- Function as backdoors to execute arbitrary commands
- Download and execute additional malicious payloads
- Manipulate what users see in their interfaces
Each successful compromise has allowed the RGB to refine their tools and techniques. They’re not starting from scratch with each target - they’re executing a tested playbook that’s specifically engineered to defeat standard cryptocurrency security controls when those controls are used in isolation.
Organizations below a certain security threshold are now at serious risk. Without comprehensive security controls including:
- Air-gapped signing systems
- Multiple layers of transaction verification
- Endpoint detection and response (EDR) systems like CrowdStrike or SentinelOne
- Regular security training and war games
They are likely to face an adversary that has already built and tested the exact tools needed to defeat their existing protections.
The New Reality of Cryptocurrency Security
This attack highlights a fundamental truth: no single security control, no matter how robust, can protect against sophisticated attackers targeting operational security. While secure code remains crucial, it must be part of a comprehensive security strategy.
Organizations must adopt new processes and controls that operate under the assumption that their infrastructure will eventually face compromise:
- Infrastructure Segmentation: Critical operations like transaction signing require both physical and logical separation from day-to-day business operations. This isolation ensures that a breach of corporate systems cannot directly impact signing infrastructure. Critical operations should use dedicated hardware, separate networks, and strictly controlled access protocols.
- Defense-in-Depth: Security controls must work in concert - hardware wallets, multi-signature schemes, and transaction verification tools each provide important protections, but true security emerges from their coordinated operation. Organizations need multiple, overlapping controls that can detect and prevent sophisticated attacks.
- Organizational Preparedness: Technical controls must be supported by comprehensive security programs that include:
- Thorough threat modeling incorporating both technical and operational risks
- Regular third-party security assessments of infrastructure and procedures
- Well-documented and frequently tested incident response plans
- Ongoing security awareness training tailored to specific roles
- War games and attack simulations that test both systems and personnel
These principles aren’t new - they represent hard-won lessons from years of security incidents in both traditional finance and cryptocurrency. Trail of Bits has consistently advocated for this comprehensive approach to security, providing concrete guidance through several key publications:
- 10 Rules for the Secure Use of Cryptocurrency Hardware Wallets (2018) - Our foundational guidance on hardware wallet security that specifically warned about the risks of hardware wallet compromise and the need for high-assurance workstations - precisely the type of issues exploited in today’s attack.
- Managing Operational Risk in Blockchain Deployments (2022) - A comprehensive framework highlighting the risks of centralized infrastructure and providing concrete guidance for implementing defense-in-depth approaches to protect high-value cryptocurrency operations.
- The Rekt Test - our simple framework for assessing basic security controls (2023) - Our simple but thorough framework for assessing basic security controls, emphasizing the critical importance of proper key management, infrastructure separation, and incident response planning - all factors that proved critical in today’s incident.
- Preventing Account Takeovers in Cryptocurrency Exchanges (2025) - A detailed analysis of attack patterns targeting cryptocurrency exchanges that predicted the industry’s pivot from technical exploits toward operational attacks.
These publications show a clear pattern that’s echoed by recent attacks: sophisticated attackers are increasingly targeting operational security vulnerabilities rather than technical flaws.
The cryptocurrency industry’s resistance to implementing traditional corporate security controls, combined with the high value of potential targets and this group’s sophisticated capabilities, suggests these attacks are likely to continue unless significant changes are made to how cryptocurrency companies approach operational security.
Moving Forward
The Bybit hack marks a new era in cryptocurrency security. Industry participants need to recognize the evolving threat landscape and invest additional resources in improving their operational security. No one understands this reality better than the security researchers who have been tracking these attacks.
Tay @tayvano_, a renowned security researcher known for exposing on-chain thefts, dissecting DPRK crypto hacks, and fiercely advocating for better blockchain security practices, summarized the current reality bluntly:
For all these reasons and more, it’s my opinion that once they get on your device, you’re fucked. The end. If your keys are hot or in AWS, they fuck you immediately. If they aren’t, they work slightly harder to fuck you. But no matter what, you’re going to get fucked.
Organizations must protect themselves through a comprehensive defense strategy combining isolation, verification, detection, and robust operational security controls. However, the time for basic security measures has passed. Organizations holding significant cryptocurrency assets must take immediate action:
- Conduct a thorough operational risk assessment using established frameworks like our “Managing Operational Risk in Blockchain Deployments”
- Implement dedicated, air-gapped signing infrastructure
- Engage with security teams experienced in defending against sophisticated state actors
- Build and regularly test incident response plans
The next billion-dollar hack isn’t a matter of if, but when. The only question is: will your organization be ready?
